Multi Factor Authentication (MFA) - 101
Quick rundown of the important bits of MFA
Table of Contents
When is MFA going to be enforced?
How do we enable MFA (if it's not yet enforced)?
Do we need to use Salesforce Authenticator for Salesforce MFA?
How do we reset the MFA authenticator for the user? (This can be for reasons such as changing the authenticator app used)
Is MFA required for External Users such as Community Users for Students?
Can users with no mobile device pass through MFA?
Salesforce's official MFA FAQ will be our first stop for most questions involving MFA:
https://help.salesforce.com/s/articleView?id=000352937&type=1
The following are some additional info or details that may be of use in MFA implementations:
When is MFA going to be enforced?
-
https://help.salesforce.com/s/articleView?id=000362737&type=1
For most of Salesforce:
Auto Enabled: January - June 2023.
Enforced: September 2023.
How do we enable MFA (if it's not yet enforced)?
-
Identity -> Identity Verification -> check the 'Require multi-factor authentication (MFA) for all direct UI logins to your Salesforce org'.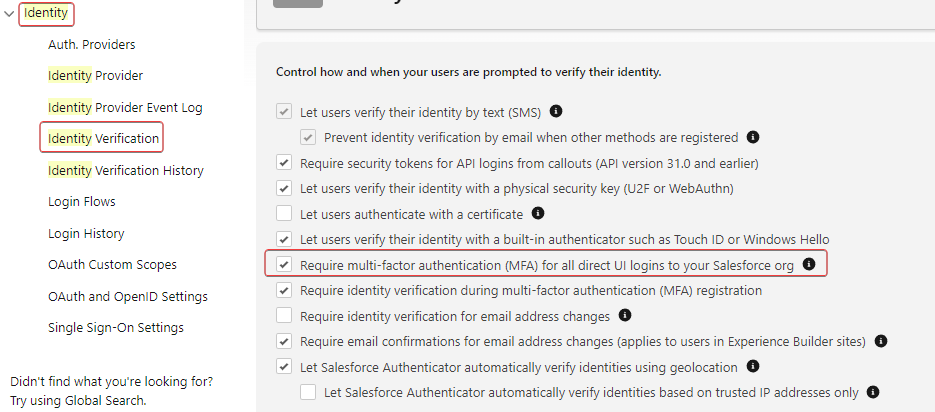
This will enable MFA for ALL users into the org (unless they are part of the exclusion list).
For a more specific MFA activation, add a permission set, or edit the profile and enable the option for
'Multi-Factor Authentication for User Interface Logins' under System Permission.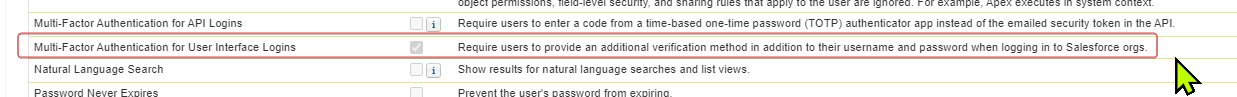
This will enable MFA only for the users with the corresponding profile or the ones given the permission set.
Do we need to use Salesforce Authenticator for Salesforce MFA?
-
No, any authenticator that supports the standardized protocol used by Salesforce MFA (which is the same one used by most MFA implementations in online applications) will work.
During the setup for Salesforce MFA, Salesforce will provide a QR code that can be scanned using any of these standard authenticators (Google Authenticator, Authy, Microsoft Authenticator, etc.).
To do so:- When prompted to set up MFA via Salesforce Authenticator (which will show up automatically the first time the user login), select 'Choose Another Verification Method' and then select the 'Use verification codes from an authenticator app'.
- A QR code would be generated, and using the authenticator app of the user's choice, they can then scan the QR code which will then allow the authenticator app to show the dynamically generated key.
- Enter the key into the field below the QR code and that should complete the setup.
- When prompted to set up MFA via Salesforce Authenticator (which will show up automatically the first time the user login), select 'Choose Another Verification Method' and then select the 'Use verification codes from an authenticator app'.
How do we reset the MFA authenticator for the user? (This can be for reasons such as changing the authenticator app used)
-
Go to Setup -> Users -> User detail.
Click "Disconnect" next to App Registration: OTP Authenticator, if the user used an Authenticator app that isn't Salesforce Authenticator: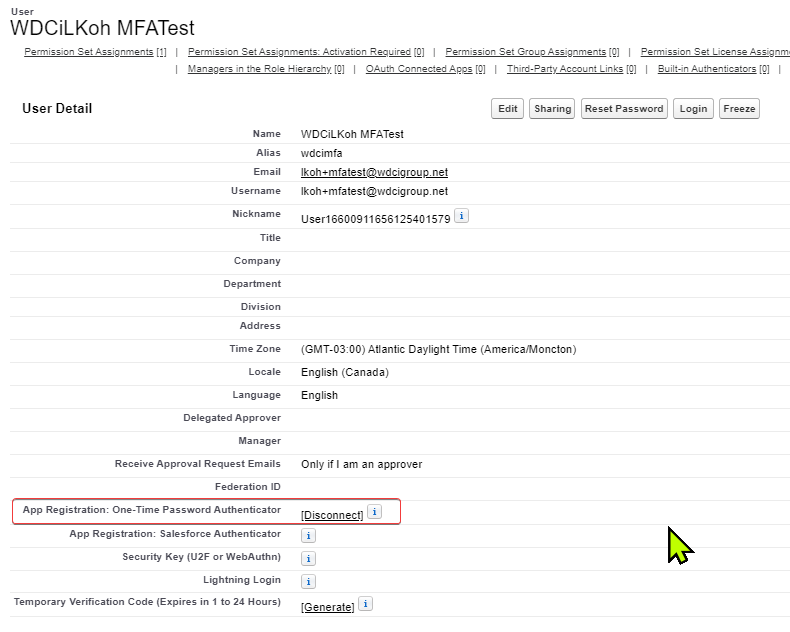
If the user instead used Salesforce Authenticator for MFA, then the disconnect link will show up next to 'App Registration: Salesforce Authenticator'.
And if the user used U2F physical security key (explained more in the later part of this article), then the disconnect link will show up next to 'Security Key (U2F or WebAuthn)'.
Once disconnected, the user will be prompted to set up their MFA again the next time they log in.
Note that only users with the system permission to do this (such as System Administrator) can access and disconnect the aforementioned link.
Is MFA required for External Users such as Community Users for Students?
-
No, as per Salesforce documentation:
https://help.salesforce.com/s/articleView?id=000352937&type=1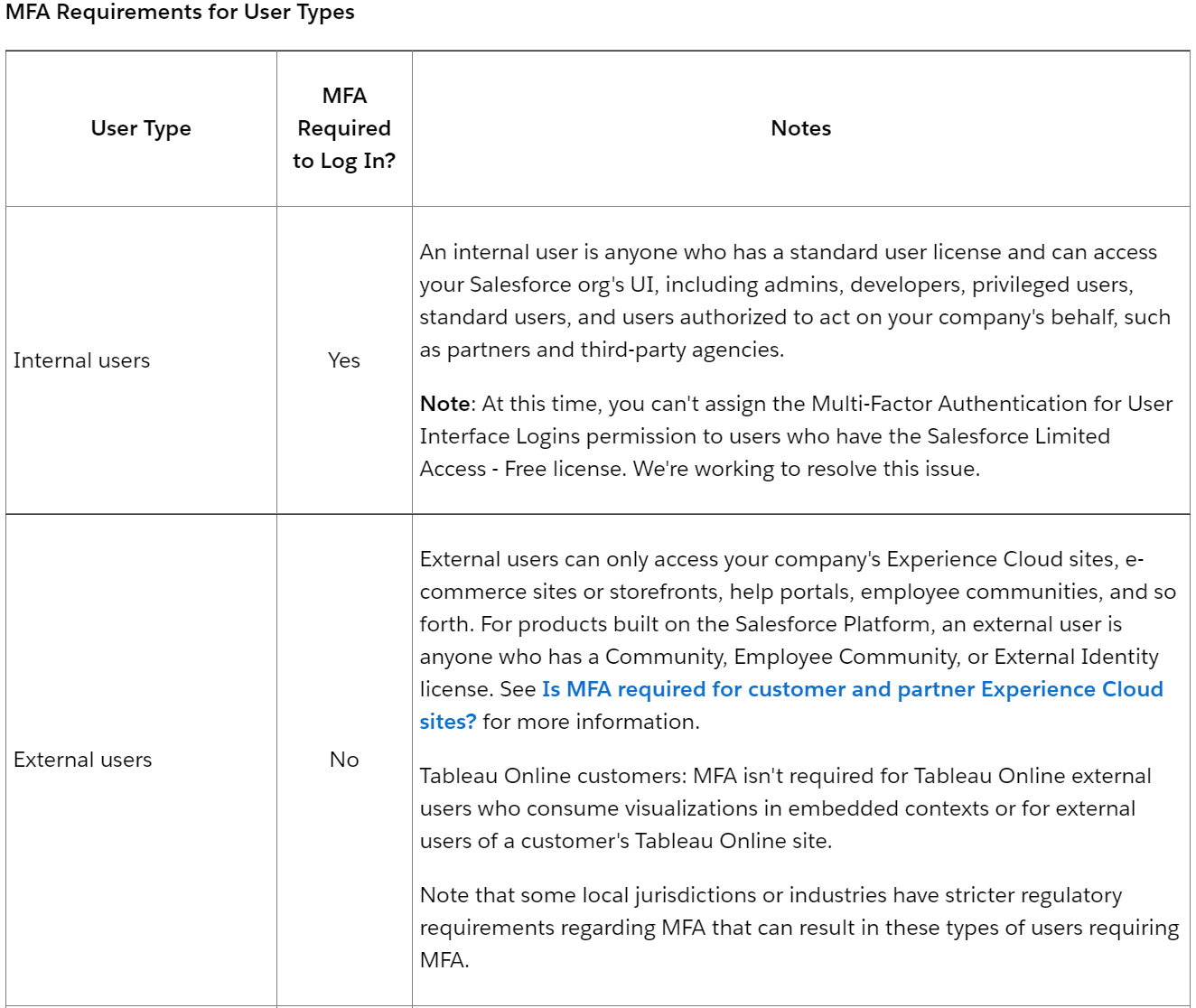
As far as RIO Education is concerned, this means that there is no change for the Students in both registration or login process, whether MFA is enabled or not.
Can users with no mobile device pass through MFA?
-
Yes, for users that either do not possess a mobile device, or do not wish to install an authentication app, there are several options to pass through MFA, and we will lay out some of the recommended options by Salesforce below.
Note however that the following options need to be enabled in the Identity Verification settings, or Session Settings which also includes it (either will work).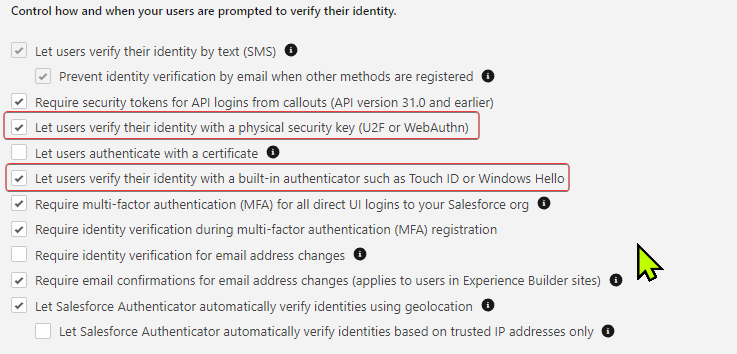
Once these options are enabled, the user will be presented with 2 additional options for authenticating during the MFA set-up on top of the default Salesforce / external authenticator app, which are:
1. 'Use a built-in authenticator on your device', and,
2. 'Use a Universal Second Factor (U2F) or WebAuthn (FIDO2) key'.
Here's a short summary of what each of them is, to help the customer decide whether they are a good option for their situation:
1. Built-in Authenticator
This refers to a physical biometric authentication system that is available in the PC/computer (whether built-in or in the form of extra attachment) used to access Salesforce, and includes a variety of things such as:
a) Windows Hello
This utilizes either as special camera designed to be able to read the user's face profile which comes prebuilt into a number of Windows laptops, as well as being available as a separate camera that can be attached to monitors like the example above or it can also utilize any built in fingerprint scanner in the PC/laptop. Note that in either case (camera or fingerprint reader) the device in question must be setup first and registered with Windows Hello in the Windows Sign In Options.
Advantage: - Relatively cheap hardware with the camera being available for less than USD 40 and can be added to most Windows PC, while fingerprint scanner can be had for USD 10 or even less.
- Simple to use and for the camera option it requires no physical touch as the user simply look at the camera when prompted.
Disadvantage: - If the user accesses the Salesforce instance from multiple machines, each machine needs to be configured separately to store the user's face profile (when using the camera) or fingerprint profile (when using the fingerprint reader) because the information is not shared. It's stored securely in the local machine and this also means that each machine must have a Windows Hello capable camera or fingerprint reader.
b) Touch ID
Fingerprint-based authentication which functions much like any other fingerprint biometric reading, and requires the user to present their fingerprint on the reader to pass through. This is only applicable to devices compatible with Touch ID.
Advantage: - No camera is required, potentially a boon if there is a concern regarding the camera feed (though note that many Windows Hello camera comes with a privacy shutter built-in and Windows Hello can also use fingerprint reader).
- Comes builtin into most recent Apple Devices.
Disadvantage: - Same disadvantage as Windows Hello in terms of requiring each device used to access to be configured.
- Touch ID being an Apple service has limited functionality outside the Apple app and product.
2. Physical Security Key (U2F or WebAuthn),
This refers to a physical security key with either a USB interface, NFC, or even Bluetooth, depending on the model of the key in question that is available from various vendors for purchase (example: Yubikey from Yubico, Google Titan from Google).
Once the key is linked with Salesforce during the MFA set-up, the user will be prompted to insert the key into the computer's USB (the most common option), or,
to bring the key close to the NFC reader / Bluetooth receiver (if the key supports it and the computer has either function) whenever Salesforce requires MFA authentication.
There may also be additional steps such as typing in PIN number associated with the key in question (also set-up during the MFA process), and the user will be prompted to provide them during the MFA authentication.
Advantage: - The security key is a physical key, it can be carried by the user everywhere much like a regular key so the user can log into Salesforce from any computer, even if they never set up MFA through that computer.
This is in contrast with Windows Hello or Touch ID which require a biometric reading device (in either the form of a special camera or fingerprint reader) and need to set up Windows Hello or Touch ID on each computer.
Disadvantage: - Unlike Windows Hello or Touch ID, the physical key can be lost much like a regular key with a similar security risk.